In the middle of December I renewed the SSL certificate of one of my Domino servers (mobil.madicon.de) and subsequently started the obligatory SSL server test of Qualys SSL Labs.
Indication of impending downgrade due to TLS 1.0
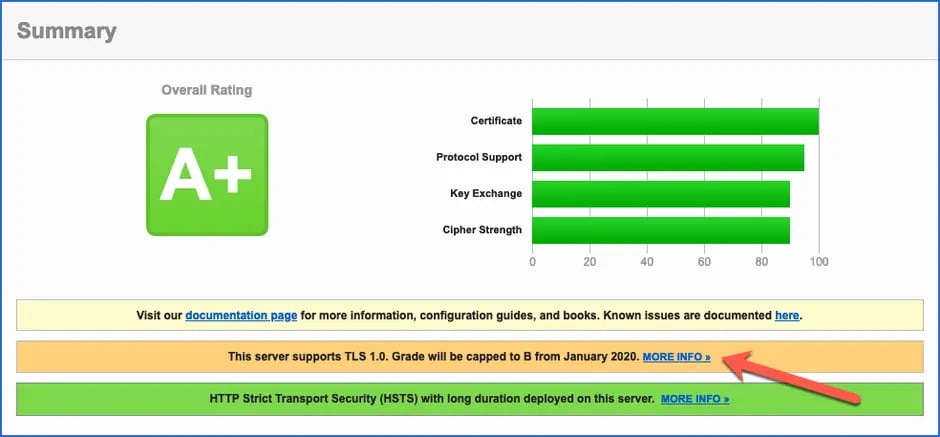
Result of the SSL Server Test - Warning about downgrade because of TLS 1.0
The rating of "A+" was OK, but the reference (marked with the red arrow in the screenshot) to the downgrade to "Grade B" from January 2020 was reported. Cause: my Domino server still supported TLS 1.0!
This was also confirmed by a look at the "Protocols" section of the results:
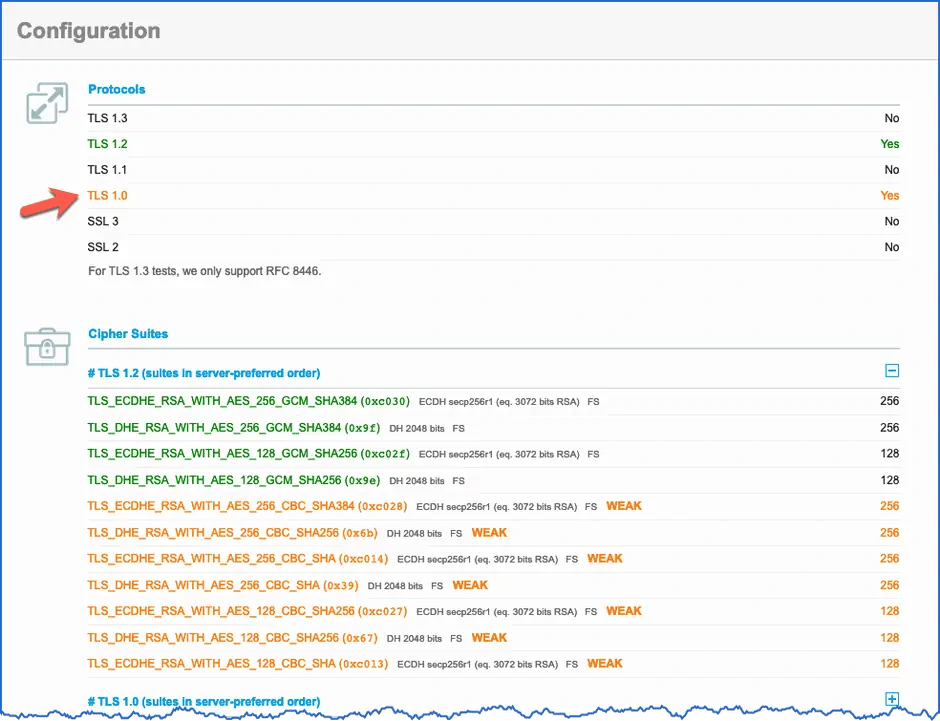
Result of the SSL Server Test - TLS 1.0 is active
Additionally you can see that several of the used ciphers are classified as "weak".
Disabling the TLS 1.0 protocol
There is a parameter for this in the NOTES.INI file of the Domino Server:
SSL_DISABLE_TLS_10=1
This parameter can be activated by the Domino Server configuration document (or in the NOTES.INI file directly):
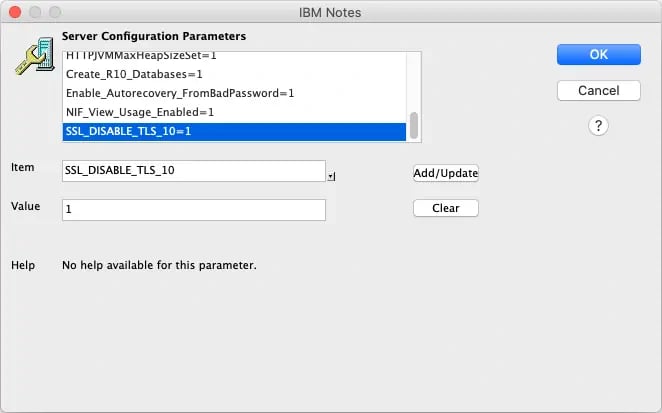
NOTES.INI parameter SSL_DISABLE_TLS_10 in the configuration document
A further analysis using the SSL server test confirms the deactivation of the TLS 1.0 protocol.
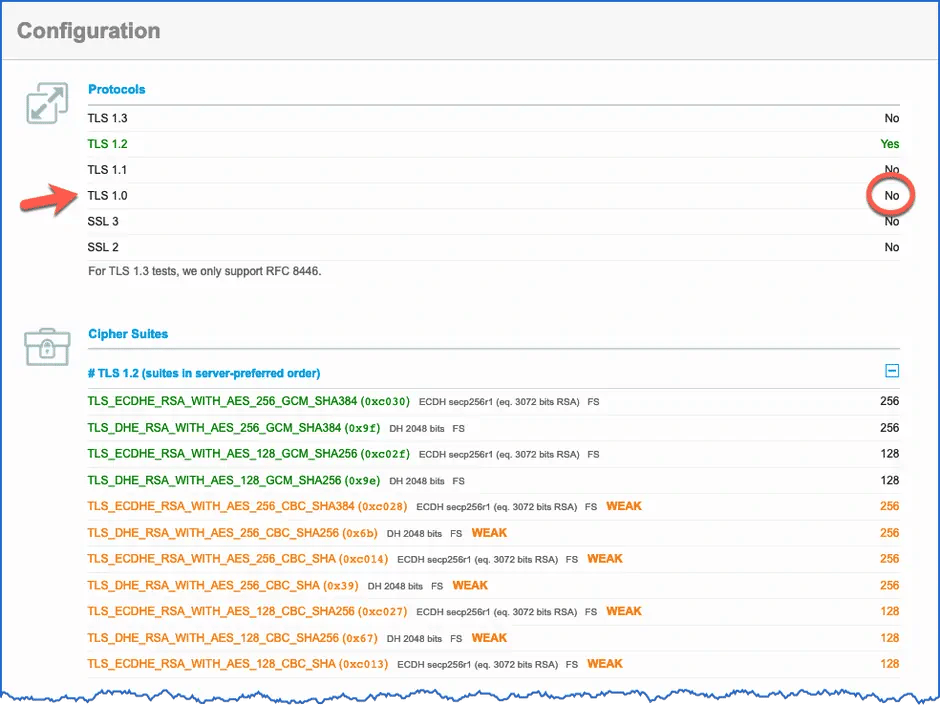
Result of the SSL Server Test - TLS 1.0 is disabled
Customizing Ciphers
Since Domino version 10 the actively used ciphers can be adjusted in the server document (tab: 'Ports...' -> 'Internet Ports...').
The use of the NOTES.INI parameter "SSLCipherSpec" (from Domino version 9.0.1 FP5, more information here) is no longer necessary.
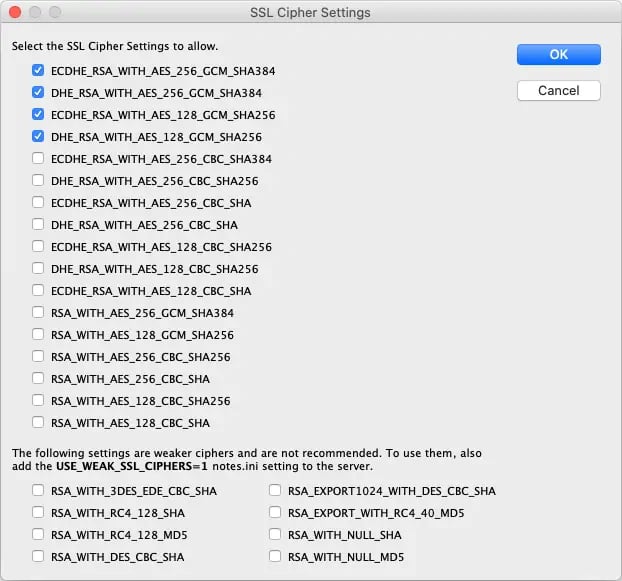
SSL Chipher Settings Domino 10 Directory
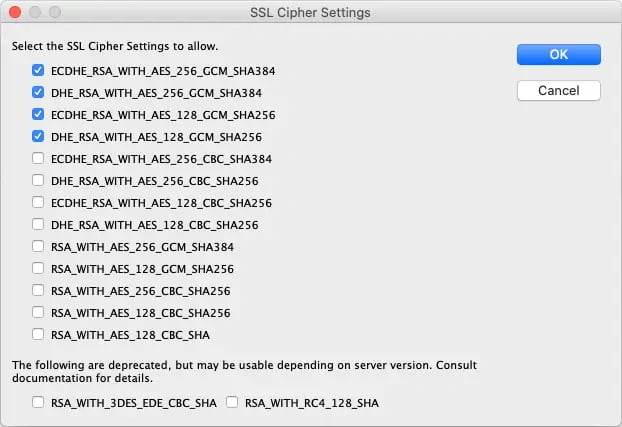
SSL Chipher Settings Domino 11 Directory
The result after switching off all ciphers classified as "weak" by SSL server tests:
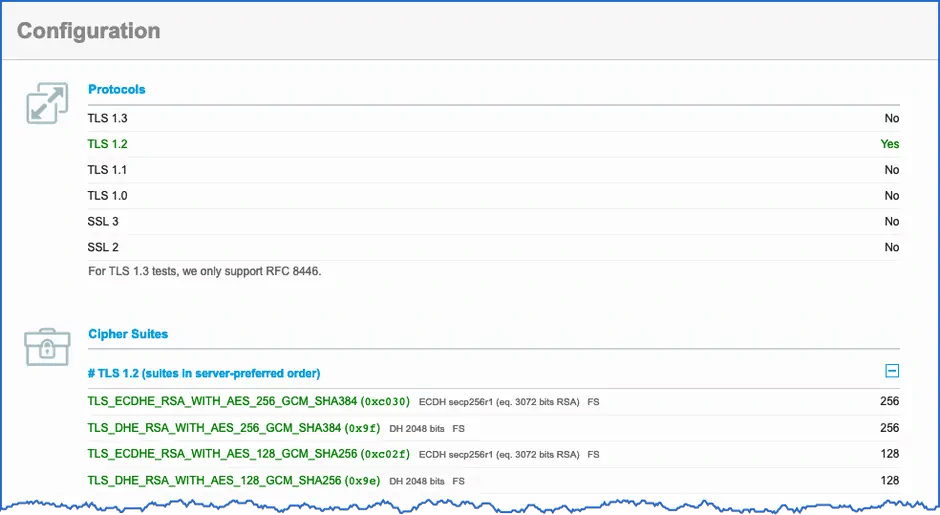
Result of the SSL Server Test - TLS 1.0 disabled, only strong ciphers
Hints
- If you have only these 4 ciphers (as shown in the screenshot above) activated, older applications or devices may not work anymore - this should be checked.I only use Traveler (with HCL Verse on the iPhone) and Verse on Premises in current browsers - it all works fine.
- If you have only activated these 4 ciphers (as shown in the screenshot above), the NOTES.INI parameter "SSL_DISABLE_TLS_10=1" is no longer required to disable the TLS 1.0 protocol.
One more thing...
Maybe you noticed the green (= good web server settings) message in the first screenshot?
HTTP Strict Transport Security (HSTS) with long duration deployed on this server
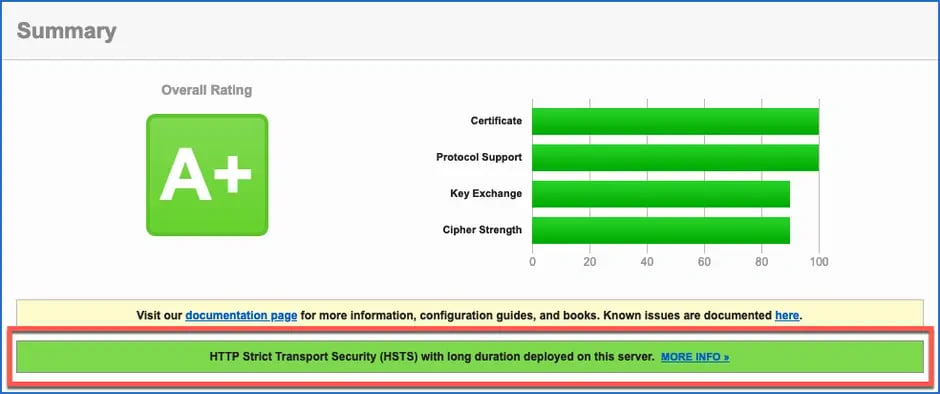
Result of the SSL Server Test - HTTP Strict Transport Security
This makes the Domino Server even more secure as a web server:
HTTP Strict Transport Security (HSTS) is a web security policy mechanism that helps to protect websites against protocol downgrade attacks[1] and cookie hijacking. It allows web servers to declare that web browsers (or other complying user agents) should interact with it using only HTTPS connections, which provide Transport Layer Security (TLS/SSL), unlike the insecure HTTP protocol used alone. HSTS is an IETF standards track protocol and is specified in RFC 6797.Source: HTTP Strict Transport Security
This setting can be specified for the Domino Server by this parameter in the NOTES.INI file:
HTTP_HSTS_MAX_AGE=31536000


